K-times Anonymous Authentication
1 no one not even an authority can identify users who have been authenticated within the allowable number 2 anyone can trace without help from the authority dishonest users who have been authenticated beyond the allowable number by using the records of these authentications. K-times anonymous authentication k-TAA schemes allow members of a group to be anonymously authenticated by application providers for a bounded number of times.

Anonymous Identity Authentication Mechanism For Hybrid Architecture In Mobile Crowd Sensing Networks Tao 2019 International Journal Of Communication Systems Wiley Online Library
K-TAA has application in e-voting e-cash electronic coupons and anonymous trial browsing of con-tent.

K-times anonymous authentication. K-times anonymous authentication k-TAA schemes allow members of a group to be anonymously authenticated by application providers for a bounded number of times. 1 no one not even an authority can identify users who have been authenticated within the allowable number 2 anyone can trace without help from the authority dishonest users who have been authenticated beyond the allowable number by using the records of these authentications. Since there are only k search tag bases if a user has been authenticated for more than k times the user must have used one of the search tag bases t i at least twice.
The proposed scheme has two features. To do so users first register to. Dynamic k-times anonymous authentication k-TAA schemes allow members of a group to be authenticated anonymously by application providers for a bounded number of times where application providers can independently and dynamically grant or revoke access right to members in their own group.
In this paper we construct a dynamic k-TAA scheme with space and time complexities of Ologk. Dynamic k-times anonymous authentication k-TAA schemes allow members of a group to be authenticated anonymously by application providers for a bounded number of times where application providers can independently and dynamically grant or revoke access right to members in their own group. K-TAA has application in e-voting e-cash electronic coupons and anonymous trial.
Extended abstract allowable number k-times anonymous authentication allow user group signature trial browsing unnecessary ability cumbersome inquiry user participation many time electronic coupon authentication scheme. Therefore anyone can decide whether some user is authenticated beyond allowed number of times. Dynamic k-times anonymous authentication k-TAA schemes allow members of a group to be authenticated anonymously by application providers for a bounded number of times where application providers can independently and dynamically grant or revoke access right to members in their own groupIn this paper we construct a dynamic k-TAA scheme with space and time complexities of O.
In k-times anonymous authentication k-TAA schemes members of a group can be anonymously authenticated to access applica- tions for a bounded number of times determined by. Japan Advanced Institute of Science and Technology JAIST Repository httpsdspacejaistacjp Title A Selectable k-Times Relaxed Anonymous. The proposed scheme has two features.
In the next time period user can automatically get another K-times. Some promising applications are e-voting e-cash e-coupons and trial browsing of contents. Adshelpatcfaharvardedu The ADS is operated by the Smithsonian Astrophysical Observatory under NASA Cooperative Agreement NNX16AC86A.
K-times anonymous authentication k-TAA schemes allow members of a group to be anonymously authenticated by application providers for a bounded number of times. A k-Times Anonymous Authentication k-TAA scheme TFS04NN05 allows users to be authenticated anonymously so long as the number of times that they are authenticated is within an allowable number. We propose an authentication scheme called k-times anonymous authentication k-TAA that satisfies the three requirements mentioned in the previous sec-tion.
Dynamic k-times anonymous authentication k-TAA schemes allow members of a group to be authenticated anonymously by application providers for a bounded number of times where application providers can independently and dynamically grant or revoke access right to members in their own group. In this paper we extend k-TAA model to dynamic k-TAA in which. A k-Times Anonymous Authentication k-TAA scheme allows users to be authenticated anonymously so long as the number of times that they are authenticated is within an allowable number.
In the next time period user can automatically get another K-times authentication permission. In a periodic K-times anonymous authentication system user can anonymously show credential at most K times in one time period. K -TAA has application in e-voting e-cash electronic coupons and anonymous trial browsing of content.
In a periodic K-times anonymous authentication system user can anonymously show credential at most K times in one time period. Dynamic k-times anonymous authentication k-TAA schemes allow members of a group to be authenticated anonymously by application providers for a bounded number of times where application. An authority called the group manager first registers users in the proposed scheme.
K-times anonymous authentication k-TAA schemes allow members of a group to be anonymously authenticated by application providers for a bounded number of timesk-TAA has application in e-voting e-cash electronic coupons and anonymous trial browsing of contentIn this paper we extend k-TAA model to dynamick-TAA in which application providers can independently grant or revoke users from. Each application providerAP then publishes the number of times a user is allowed to use their application. We propose an authentication scheme in which users can be authenticated anonymously so long as times that they are authenticated is within an allowable number.
Hence in such a case anyone can find search tags τand νwhich satisfy τ ν t i x. K-times anonymous authentication k-TAA scheme TFS04 so that users of a group can access applications anonymously while application providers APs can decide the number of times users can access their applications. The proposed scheme has two features that allow 1 no one not even an authority identify users who have been authenticated within the allowable number and that allow 2 anyone to trace without help from the authority dishonest users who have been authenticated beyond the allowable number by using the records of these authentications.
The scheme not only o ers a time restriction mechanism to well-known group signature schemes.

Anonymous Identity Authentication Mechanism For Hybrid Architecture In Mobile Crowd Sensing Networks Tao 2019 International Journal Of Communication Systems Wiley Online Library
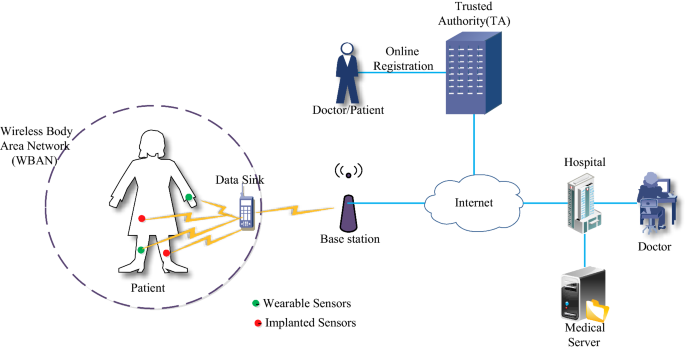
An Efficient Anonymous Authentication And Confidentiality Preservation Schemes For Secure Communications In Wireless Body Area Networks Springerlink

Enable Both Windows Authentication And Anonymous Authentication In An Asp Net Core App Stack Overflow

Posting Komentar untuk "K-times Anonymous Authentication"